F5 | F5 BIG-IP | F5 BIG-IP ASM | IT Security
Data Guard And PCI Compliance
A. The Overview
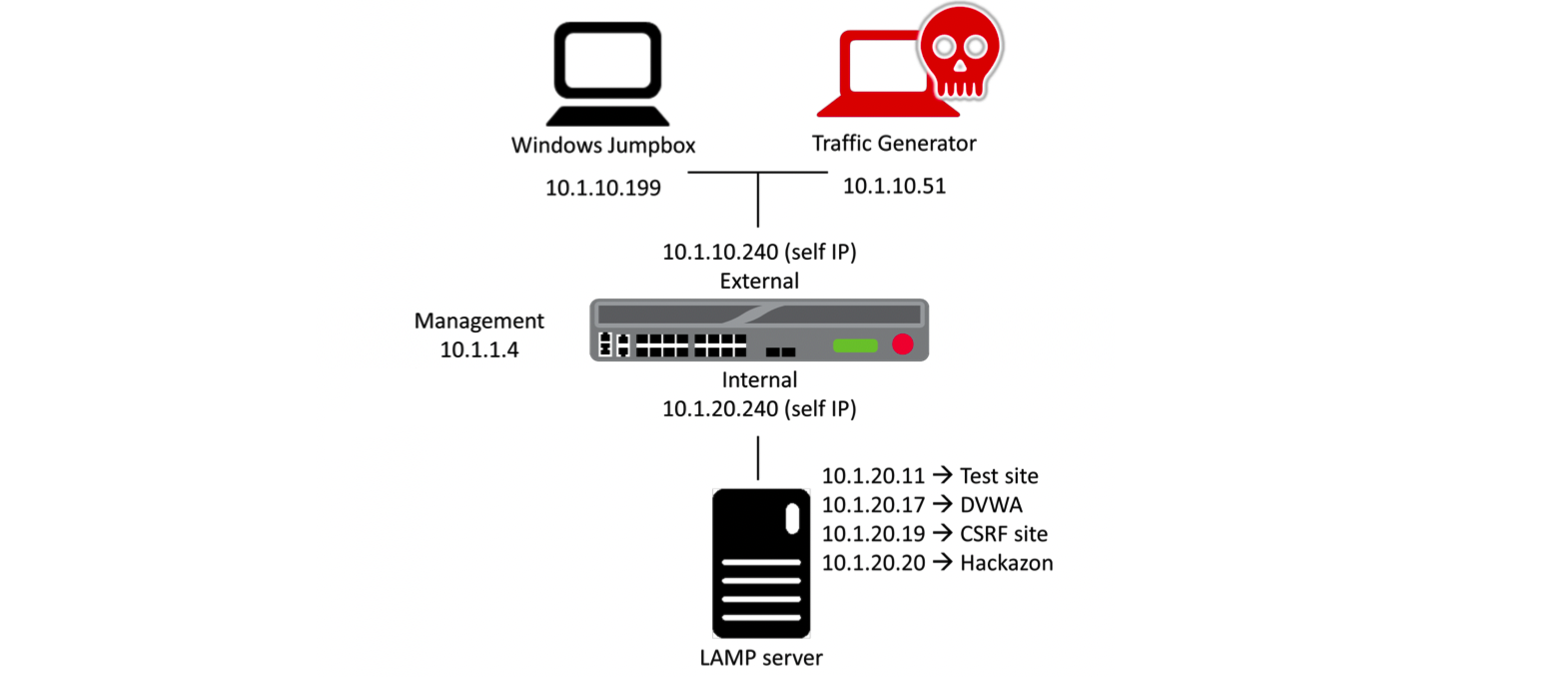
1. Network Architecture Diagram
- F5 BIG-IP Information:
- TMOS version 15.1.0.2
- Resource Provisioning: Local Traffic (LTM), Application Security (ASM), Fraud Protection Service (FPS)
- Attempt two well-known attacks against the DVWA application
- SQL Injection, Cross-Site Scripting
- Create a security policy for the DVWA application using Rapid Deployment Template
- Re-attempt to attack the DVWA application
- View the F5 BIG-IP AWAF Event Log
- Attempt the Information Leakage scenario
- View the Current Security Policy and PCI Compliance Report
- Enable Data Guard and View the PCI Compliance Report
- Re-attempt the Information Leakage scenario
- View the PCI Compliance Report
- Attempt two well-known attacks against the DVWA application
- SQL Injection, Cross-Site Scripting
- Create a security policy for the DVWA application using Fundamental Template
- Re-attempt to attack the DVWA application
- View the F5 BIG-IP AWAF Event Log and Security Reports
B. LAB02: Use Data Guard and Attain PCI Compliance
1. Verify and Fix The PCI Compliance
- Use the previous LAB01 setup
- Open Firefox web browser, and connect to DVWA VS http://10.1.10.35/
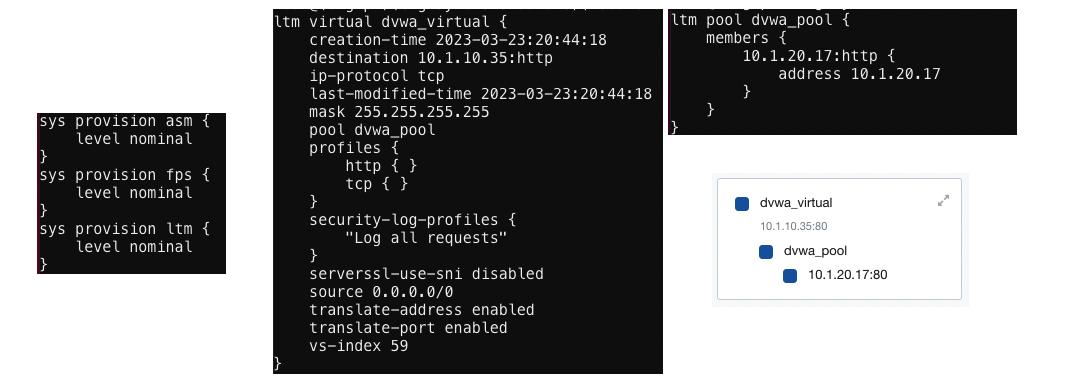
- Review the current BIG-IP AWAF configuration
- dvwa_virtual is a standard HTTP virtual server that listens on 10.1.10.35.
- Note that this virtual server contains the default http profile.
- An HTTP profile is required to protect against application layer attacks.
- The current Security Policy isn’t yet configured to protect against information leakage
- dvwa_virtual is a standard HTTP virtual server that listens on 10.1.10.35.
- Review PCI Compliance Report
- The PCI Compliance Report lists each security measure required to comply with PCI-DSS 3.2, and indicates which measures are relevant, or not relevant, to the ASM.
- For security measures that are relevant to the ASM, the report indicates whether this ASM appliance complies with PCI-DSS 3.2.
- For security measures that are not relevant to the ASM, the report explains what action you must take to make this ASM appliance comply with PCI-DSS 3.2.
- Navigate to: Security ›› Reporting : Application : PCI Compliance
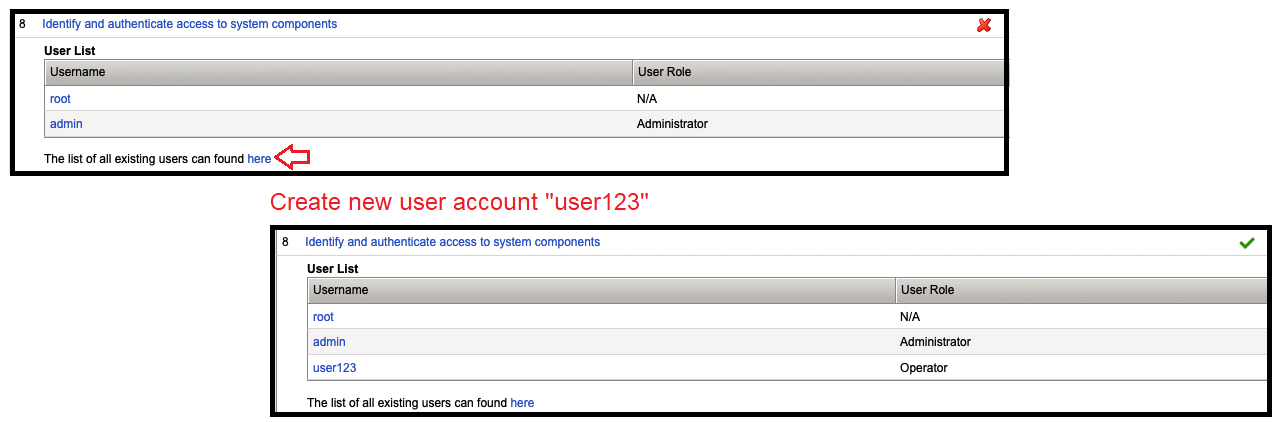
- Click “Identify and authenticate access to system components“
- To meet PCI compliance, we need to have unique usernames for all BIG-IP system users.
- To fix this compliance issue, click “here”
- Directed to: System ›› Users : User List
- User Name: user123
- Password: xxx
- Role: Operator
- Click “User is forced to change password every 90 days“
- To meet PCI compliance, we need to have a password policy on the BIG-IP system.
- To fix this compliance issue click “Fix Automatically”.
- The BIG-IP system automatically creates a password policy requiring BIG-IP users to change their passwords every 90 days.
- System ›› Users : Authentication
- Maximum Duration: 99999 days -> 90 days
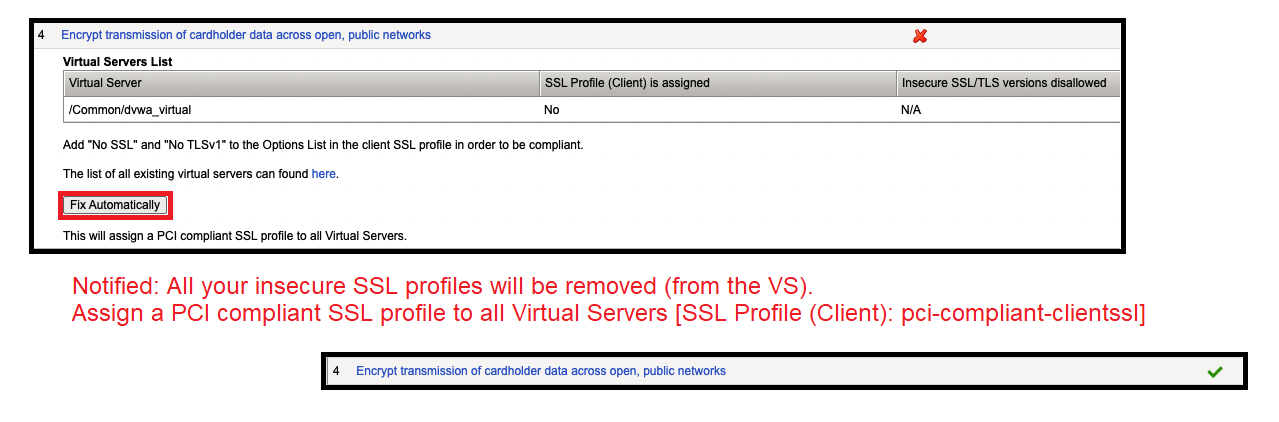
- Click “Encrypt transmissions of cardholder data across open, public networks“
- To meet PCI compliance, our web application must be using HTTPS and secure certificates.
- To fix this compliance issue click “Fix Automatically”.
- Add “No SSL” and “No TLSv1” to the Options List in the client SSL profile in order to be compliant.
- Notified: All your insecure SSL profiles will be removed (from the VS).
- This will assign a PCI compliant SSL profile to all Virtual Servers.
- dvwa_virtual > SSL Profile (Client): pci-compliant-clientssl
- Manually modify the VS dvwa_virtual “Service Port” to 443.
- Click “Protect stored cardholder data“
- To meet PCI compliance, enable Data Guard in the Security Policy to protect credit card numbers.
- Click “Identify and authenticate access to system components“
- The PCI Compliance Report lists each security measure required to comply with PCI-DSS 3.2, and indicates which measures are relevant, or not relevant, to the ASM.
2. Verify and Fix The Information Leakage
- Open Firefox web browser, and connect to DVWA VS https://10.1.10.35/
- Identify the threat of Information Leakage
- Information Leakage:
- Sensitive information may be present within HTML comments, error messages, source code, or simply left in files which are accessible by remote clients.
- In addition attackers can manipulate the application to reveal classified information like credit card numbers.
- This can lead to the disclosure of sensitive system information which may be used by an attacker to further compromise the system.
- Login to DVWA using a hacker user
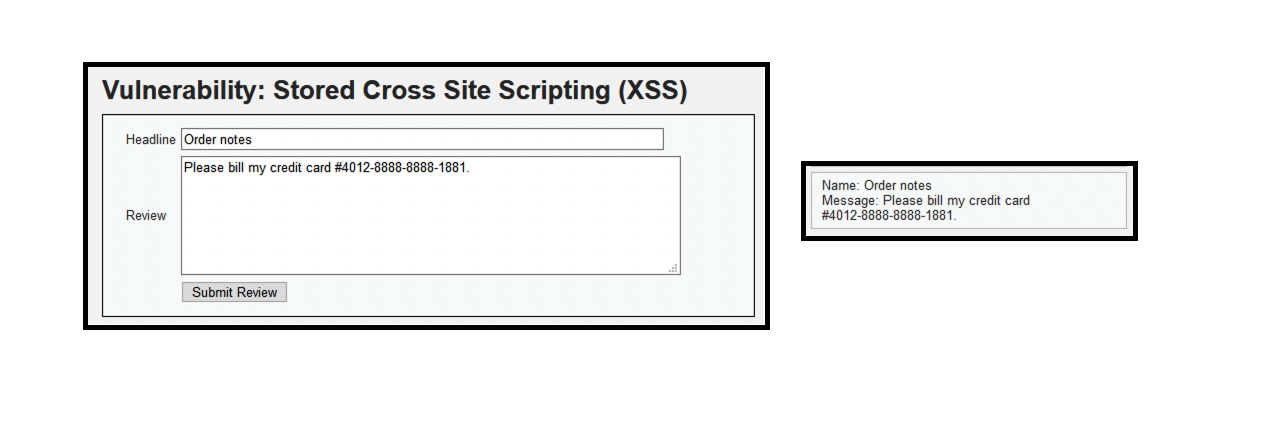
- Navigate to “XSS stored” menu
- (1) Please bill my credit card #4012-8888-8888-1881.
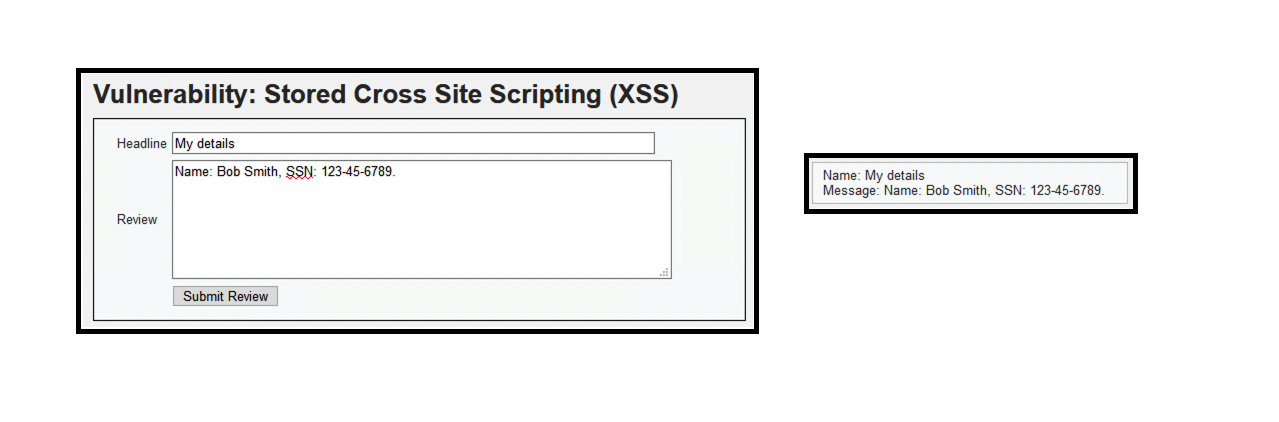
- (2) Name: Bob Smith, SSN: 123-45-6789.
- Credit card numbers and Social Security Number are being sent in cleartext in the HTTP response. This is known as information leakage and is not PCI compliant.
- Information Leakage:
- To enable Data Guard in the Application Security Policy
- Security ›› Application Security : Data Guard
- Data Guard: Enabled
- Notice that by default Data Guard protects both credit card numbers and US social security numbers.
- Save & Apply Policy
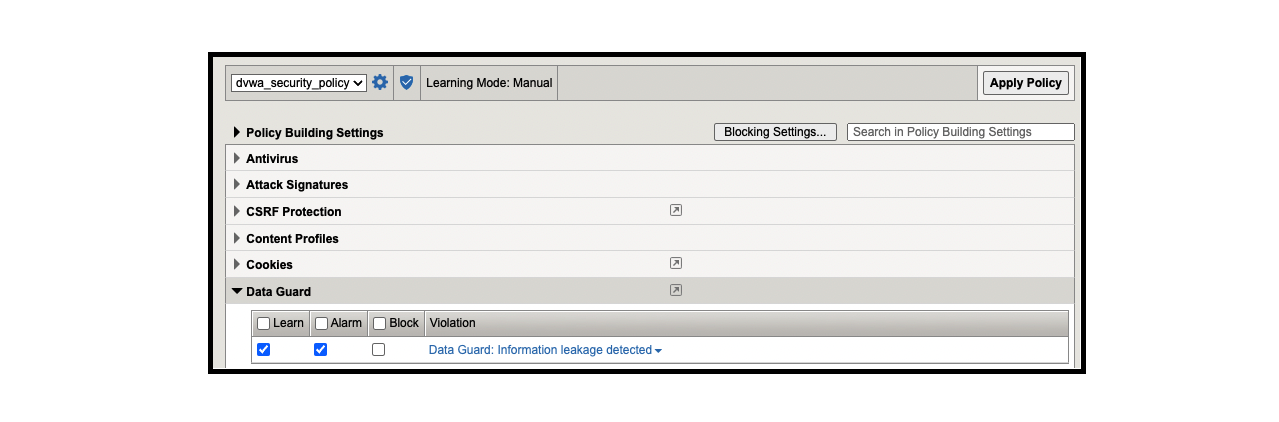
- Security ›› Application Security : Policy Building : Learning and Blocking Settings
- Data Guard
- Learn: checked
- Alarm: checked
- Block: uncheck this
- In this case, we want to allow the HTTP transaction while BIG-IP AWAF masks the leaked sensitive information.
- Save & Apply Policy
- Data Guard
- Login to (https) DVWA using a hacker user
- Navigate to “XSS stored” menu
- (1) Please bill my credit card #4012-8888-8888-1881.
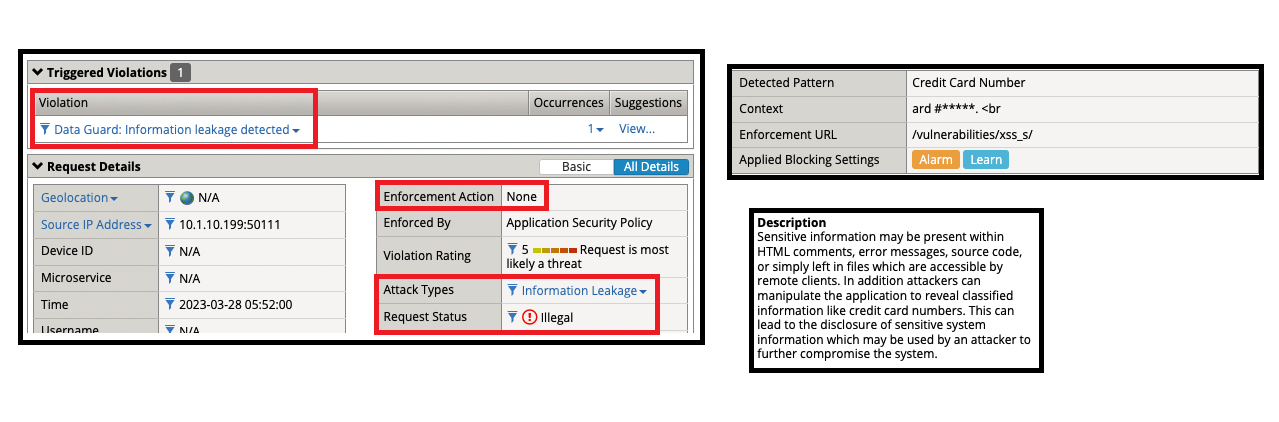
- Credit card numbers are now being masked by BIG-IP ASM, except for the last four digits.
- Data Guard: Information leakage detected
- Detected Pattern: Credit Card Number
- (2) Name: Bob Smith, SSN: 123-45-6789.
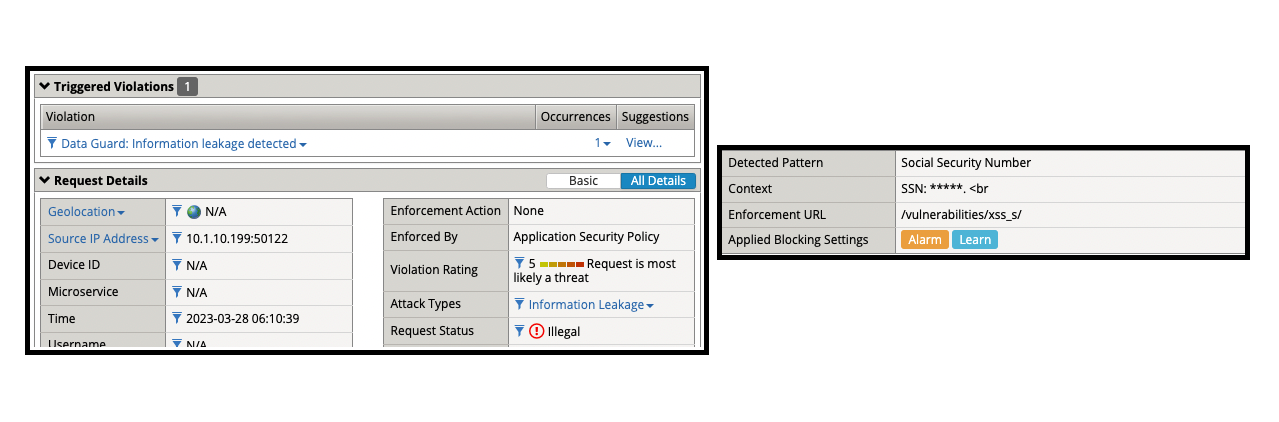
- Social security numbers are also being masked by BIG-IP ASM.
- Data Guard: Information leakage detected
- Detected Pattern: Social Security Number
- (1) Please bill my credit card #4012-8888-8888-1881.
- Security ›› Application Security : Data Guard
Supplemental Links
- None