[F5 SSLO] LAB 1 – Application Access Via Transparent Forward Proxy
The SSLO configuration as a transparent forward proxy has been completed. At this point an internal client should be able to browse out to external (Internet) resources, and decrypted traffic will flow across the security services.3. Test The Solution
- View SSLO access logs
- Client’s default gateway is 10.1.10.100 (F5 SSLO Self-IP)
- https://www.google.com/
- URL Category: Search_Engines_and_Portals
- Matched Policy Rule: All Traffic | Action: Intercepted

Traffic Summary
- APM Access Profile: /Common/sslo_demoL3.app/sslo_demoL3_accessProfile
- LTM Virtual Server: /Common/sslo_demoL3.app/sslo_demoL3-in-t-4
- L4 Connection: tcp 10.1.10.50:40204 -> 74.125.130.106:443
- ClientSSL: TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256
- ServerSSL: TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256
- Application: L7 https (www.google.com)
- decryption-status: decrypted
- duration: 139350 msec
- service-path: ssloSC_all_services
- client-bytes-in: 3921
- client-bytes-out: 5015
- server-bytes-in: 8416
- server-bytes-out: 3916
- client-tls-handshake: completed
- server-tls-handshake: completed
- reset-cause: ‘NA’
- policy-rule: ‘All Traffic’
- url-category: /Common/Search_Engines_and_Portals
- ingress: /Common/client-vlan
- egress: /Common/outbound-vlan
info tmm[27190]: 01c40000:6: /Common/sslo_demoL3.app/sslo_demoL3_accessProfile:Common:555d6c57: /Common/sslo_demoL3.app/sslo_demoL3-in-t-4 Traffic summary - tcp 10.1.10.50:40204 -> 74.125.130.106:443 clientSSL: TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256 serverSSL: TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256 L7 https (www.google.com) decryption-status: decrypted duration: 139350 msec service-path: ssloSC_all_services client-bytes-in: 3921 client-bytes-out: 5015 server-bytes-in: 8416 server-bytes-out: 3916 client-tls-handshake: completed server-tls-handshake: completed reset-cause: 'NA' policy-rule: 'All Traffic' url-category: /Common/Search_Engines_and_Portals ingress: /Common/client-vlan egress: /Common/outbound-vlan
Full logs- https://www.who.int/
- URL Category: Health_and_Medicine
- Matched Policy Rule: urlf_bypass | Action: Intercepted
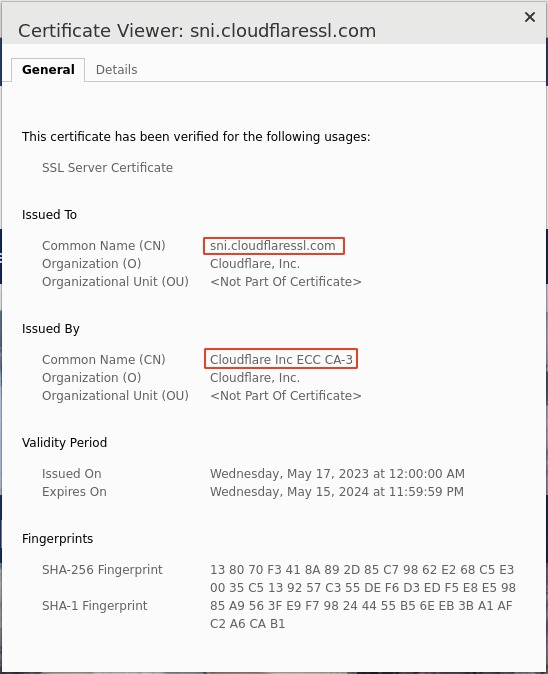
Traffic Summary
- APM Access Profile: /Common/sslo_demoL3.app/sslo_demoL3_accessProfile
- LTM Virtual Server: /Common/sslo_demoL3.app/sslo_demoL3-in-t-4
- L4 Connection: tcp 10.1.10.50:33648 -> 104.18.156.21:443
- ClientSSL: NA NA
- ServerSSL: NA NA
- Application: L7 https (www.who.int)
- decryption-status: not-decrypted
- duration: 302464 msec
- service-path: ssloSC_L2_services
- client-bytes-in: 3514
- client-bytes-out: 19919
- server-bytes-in: 2814
- server-bytes-out: 601
- client-tls-handshake: bypassed
- server-tls-handshake: completed
- reset-cause: ‘connector abort by cs service’
- policy-rule: ‘urlf_bypass’
- url-category: /Common/Health_and_Medicine
- ingress: /Common/client-vlan
- egress: /Common/NA
info tmm1[27190]: 01c40000:6: /Common/sslo_demoL3.app/sslo_demoL3_accessProfile:Common:3325642a: /Common/sslo_demoL3.app/sslo_demoL3-in-t-4 Traffic summary - tcp 10.1.10.50:33648 -> 104.18.156.21:443 clientSSL: NA NA serverSSL: NA NA L7 https www.who.int) decryption-status: not-decrypted duration: 302464 msec service-path: ssloSC_L2_services client-bytes-in: 3514 client-bytes-out: 19919 server-bytes-in: 2814 server-bytes-out: 601 client-tls-handshake: bypassed server-tls-handshake: completed reset-cause: 'connector abort by cs service' policy-rule: 'urlf_bypass' url-category: /Common/Health_and_Medicine ingress: /Common/client-vlan egress: NA
Full logs- The routing from Client to Internet is via F5 SSLO
- Client’s default gateway is 10.1.10.100 (F5 SSLO Self-IP)
- View SSLO access logs
- Log Settings > SSL Orchestrator Generic: Information
- tail -f /var/log/apm
- https://www.google.com/
- URL Category: Search_Engines_and_Portals
- Matched Policy Rule: All Traffic | Action: Intercepted

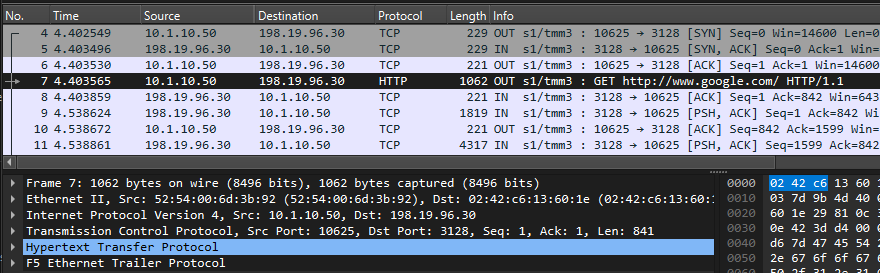

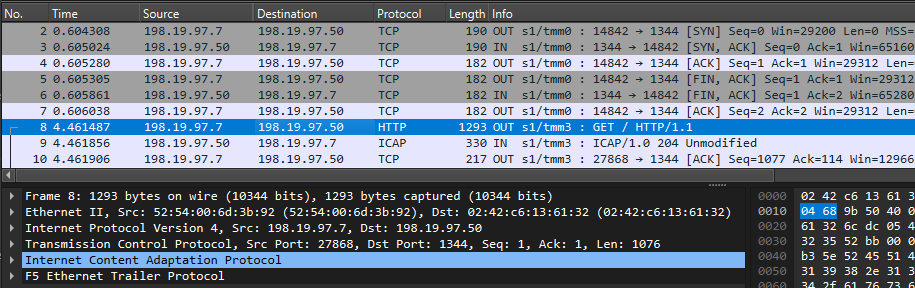


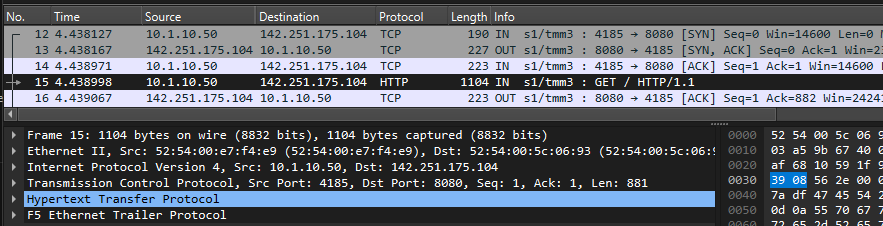
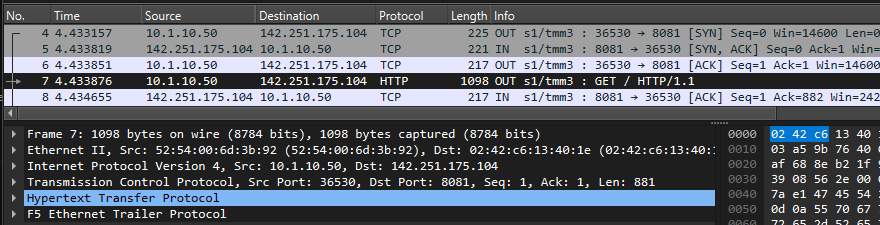

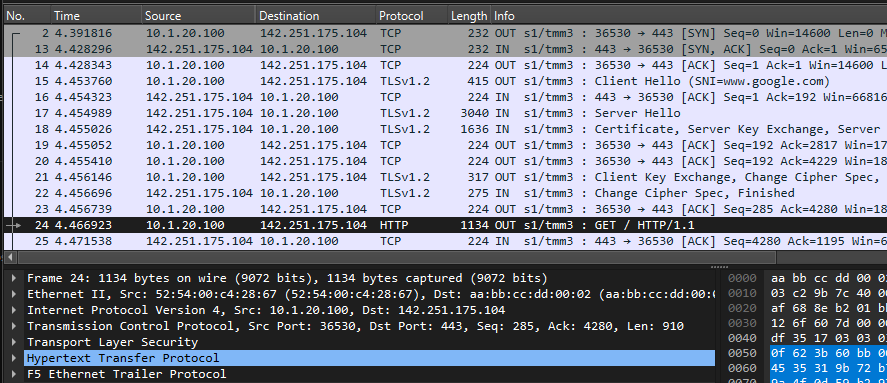
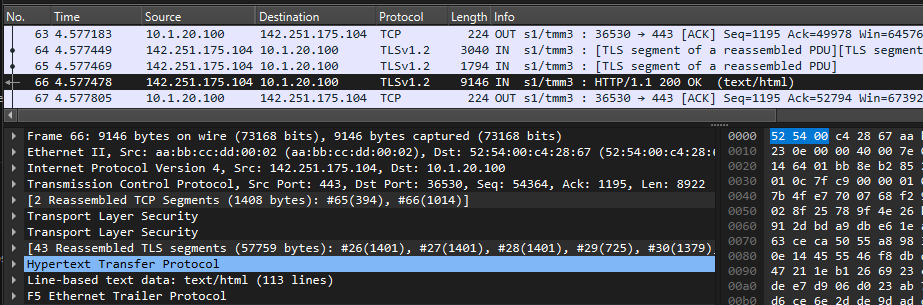

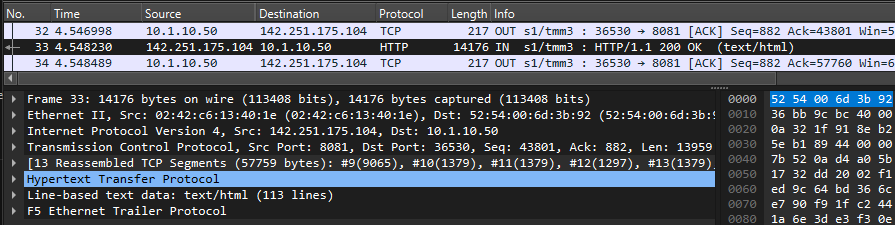
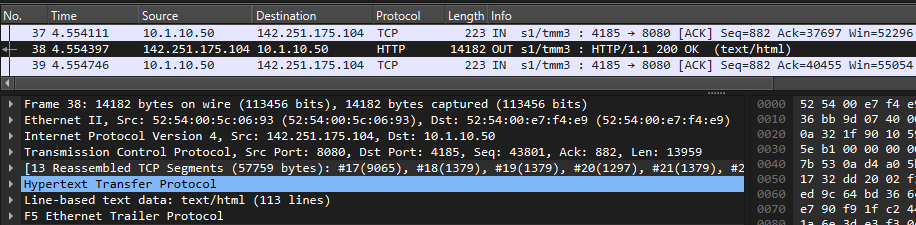



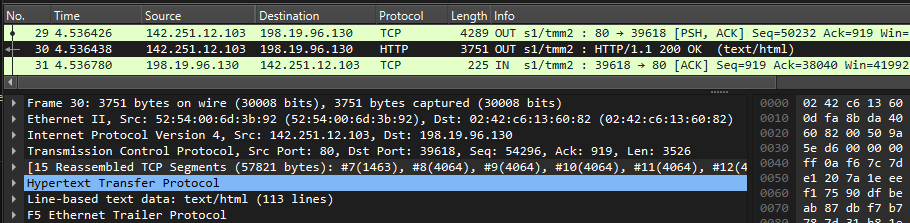
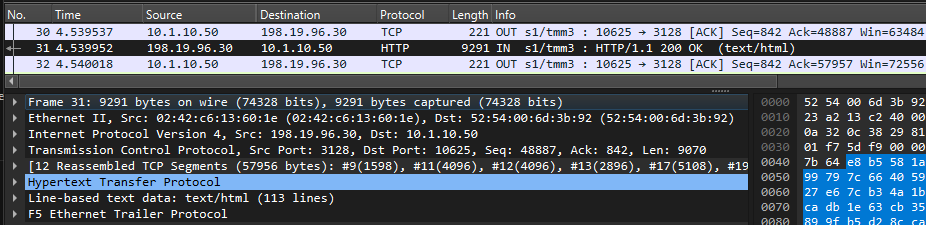
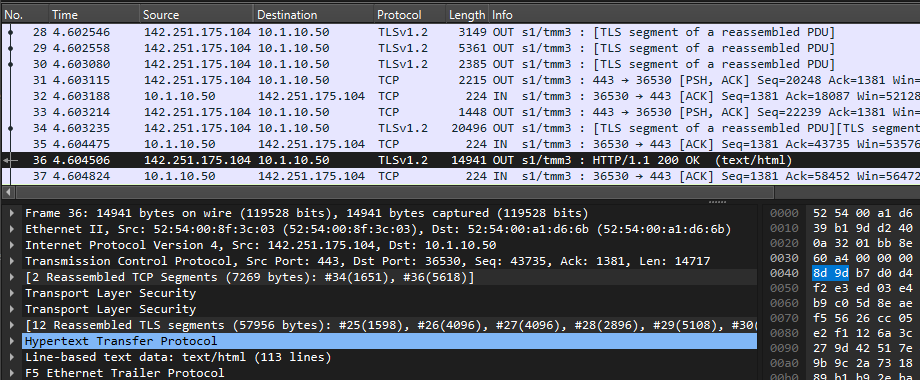
info tmm[27190]: 01c40000:6: /Common/sslo_demoL3.app/sslo_demoL3_accessProfile:Common:555d6c57: /Common/sslo_demoL3.app/sslo_demoL3-in-t-4 Traffic summary - tcp 10.1.10.50:40204 -> 74.125.130.106:443 clientSSL: TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256 serverSSL: TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256 L7 https (www.google.com) decryption-status: decrypted duration: 139350 msec service-path: ssloSC_all_services client-bytes-in: 3921 client-bytes-out: 5015 server-bytes-in: 8416 server-bytes-out: 3916 client-tls-handshake: completed server-tls-handshake: completed reset-cause: 'NA' policy-rule: 'All Traffic' url-category: /Common/Search_Engines_and_Portals ingress: /Common/client-vlan egress: /Common/outbound-vlan
Full logs- https://www.who.int/
- URL Category: Health_and_Medicine
- Matched Policy Rule: urlf_bypass | Action: Intercepted

Traffic Summary
- APM Access Profile: /Common/sslo_demoL3.app/sslo_demoL3_accessProfile
- LTM Virtual Server: /Common/sslo_demoL3.app/sslo_demoL3-in-t-4
- L4 Connection: tcp 10.1.10.50:33648 -> 104.18.156.21:443
- ClientSSL: NA NA
- ServerSSL: NA NA
- Application: L7 https (www.who.int)
- decryption-status: not-decrypted
- duration: 302464 msec
- service-path: ssloSC_L2_services
- client-bytes-in: 3514
- client-bytes-out: 19919
- server-bytes-in: 2814
- server-bytes-out: 601
- client-tls-handshake: bypassed
- server-tls-handshake: completed
- reset-cause: ‘connector abort by cs service’
- policy-rule: ‘urlf_bypass’
- url-category: /Common/Health_and_Medicine
- ingress: /Common/client-vlan
- egress: /Common/NA
info tmm1[27190]: 01c40000:6: /Common/sslo_demoL3.app/sslo_demoL3_accessProfile:Common:3325642a: /Common/sslo_demoL3.app/sslo_demoL3-in-t-4 Traffic summary - tcp 10.1.10.50:33648 -> 104.18.156.21:443 clientSSL: NA NA serverSSL: NA NA L7 https www.who.int) decryption-status: not-decrypted duration: 302464 msec service-path: ssloSC_L2_services client-bytes-in: 3514 client-bytes-out: 19919 server-bytes-in: 2814 server-bytes-out: 601 client-tls-handshake: bypassed server-tls-handshake: completed reset-cause: 'connector abort by cs service' policy-rule: 'urlf_bypass' url-category: /Common/Health_and_Medicine ingress: /Common/client-vlan egress: NA
Full logsSupplemental Links
- None