[F5SSLO LAB1-2] Access Internet Via Transparent Proxy
1. Introduction
The SSLO configuration as a transparent forward proxy has been completed.
o) To review the configuration please refer to the previous F5SSLO LAB1-1.
o) At this point an internal client should be able to browse out to external (Internet) resources.
o) The decrypted traffics will flow across the security services.1.1 Miscellaneous Details
Client's Routing- An internal client makes a request to an Internet URL
- Client traffic is routed to Internet via F5 SSLO
- Client’s default gateway is 10.1.10.100 (F5-SSLO Port-1.1 client-vlan Self-IP)
- SSL Orchestrator > Configuration > [Existing Topology] sslo_demoL3
- Log Settings > SSL Orchestrator Generic: Information
- tail -f /var/log/apm
- Google
- The SSL sessions are being terminated in F5 SSLO
- This is useful for troubleshooting purpose, to decrypt encrypted traffic between:
- Client and F5-SSLO-VS
- F5-SSLO and Web-Server (Google)
- HowTo
- Decrypting TLSv1.2 traffic via iRules command “SSL::sessionsecret”
- ltm virtual sslo_demoL3.app/sslo_demoL3-in-t-4 { rules { decrypt_ssl } }
- WHO
- The SSL sessions are established end-to-end between client and server
- They are not being terminated in F5 SSLO
2. Client Access To Google Review
URL: https://www.google.com/
- URL Category: Search_Engines_and_Portals
- Matched Policy Rule: All Traffic | Action: Intercepted
- Service Chain: ssloSC_all_services
- Service Chain Order: (1) ssloS_Proxy | (2) ssloS_DLP | (3) ssloS_TAP | (4) ssloS_FEYE | (5) ssloS_IPS
2.1 Server SSL Certificate Review

SSLO Access Logs – Traffic Summary
- APM Access Profile: /Common/sslo_demoL3.app/sslo_demoL3_accessProfile
- LTM Virtual Server: /Common/sslo_demoL3.app/sslo_demoL3-in-t-4
- L4 Connection: tcp 10.1.10.50:40204 -> 74.125.130.106:443
- ClientSSL: TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256
- ServerSSL: TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256
- Application: L7 https (www.google.com)
- decryption-status: decrypted
- duration: 139350 msec
- service-path: ssloSC_all_services
- client-bytes-in: 3921
- client-bytes-out: 5015
- server-bytes-in: 8416
- server-bytes-out: 3916
- client-tls-handshake: completed
- server-tls-handshake: completed
- reset-cause: ‘NA’
- policy-rule: ‘All Traffic’
- url-category: /Common/Search_Engines_and_Portals
- ingress: /Common/client-vlan
- egress: /Common/outbound-vlan
- Full Logs
2.2 SSL Handshake
- (1) The SSL forward proxy mechanism must first pause the client TLS handshake at the Client Hello message.
- (2) The SSL forward proxy will make a server-side connection to the remote host,
- (3) Retrieve and validate the remote server’s certificate
- (4) Re-issue (forge) a remote server certificate to local clients using a local CA, and then resume the client side handshake with the new forged certificate
- SSL Orchestrator also, by default, enables caching of these re-issued certificates to optimize throughput.
- (1) The client-side TLS handshake is immediately resumed with the cached re-issued certificate.
- In this case, the client-side TLS handshake completes immediately before initiating the server-side flow.
- Note: That irrespective of the cached certificate, SSL forward proxy can be configured to always validate the remote server certificate and does so by default:
- When OCSP or CRL validation is enabled in the SSL configuration, (Or)
- When Server Certificate Status Checking in enabled in the security policy.
- Checking the SSL Forward Proxy Cached Certs
- tmsh show ltm clientssl-proxy cached-certs clientssl-profile [profile] virtual [vip]
- tmsh show ltm clientssl-proxy cached-certs clientssl-profile ssloT_demoL3.app/ssloT_demoL3-cssl virtual sslo_demoL3.app/sslo_demoL3-in-t-4
- Clearing the SSL Forward Proxy Cached Certs
- tmsh delete ltm clientssl-proxy cached-certs clientssl-profile [profile] virtual [vip]
- tmsh delete ltm clientssl-proxy cached-certs clientssl-profile ssloT_demoL3.app/ssloT_demoL3-cssl virtual sslo_demoL3.app/sslo_demoL3-in-t-4
- A. Client -> F5 SSLO VS (send “TLSv1.2 Client Hello” via client-vlan)
- ETH II, Src: 52:54:00:a1:d6:6b (Client-MAC), Dst: 52:54:00:8f:3c:03 (F5-SSLO Port-1.1 client-vlan)
- IPv4, Src: 10.1.10.50 (Client-IP), Dst: 142.251.10.157 (adservice.google.com)
- TCP, Src Port: 60838, Dst Port: 443
- TLSv1.2, Handshake Type: Client Hello
- Random: 63cb3..
- Session ID: 5586e..
- Cipher Suites (16 suites)
- …
- Cipher Suite: TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
- Cipher Suite: TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
- Cipher Suite: TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
- …
- Extensions
- server_name name=adservice.google.com
- supported_versions TLS 1.3, TLS 1.2, TLS 1.1, TLS 1.0
- Signature Hash Algorithms (8 algorithms: Hash: SHA256/384/512 | Signature: ECDSA/RSA)
- ecdsa_secp256r1_sha256 | rsa_pss_rsae_sha256 | rsa_pkcs1_sha256
- ecdsa_secp384r1_sha384 | rsa_pss_rsae_sha384 | rsa_pkcs1_sha384
- rsa_pss_rsae_sha512 | rsa_pkcs1_sha512
- Elliptic curves point formats (ec_point_formats)
- Renegotiation info
- PSK Key Exchange Mode: PSK with (EC)DHE key establishment (psk_dhe_ke)
- F5 Ethernet Trailer Protocol
- Virtual Server: /Common/sslo_demoL3.app/sslo_demoL3-in-t-4
- Flow ID: 0x0000400001998e00 | Peer ID: 0x0000400001998700
- B. F5 SSLO VS -> Client (send “TLSv1.2 Server Hello” via client-vlan)
- ETH II, Src: 52:54:00:8f:3c:03 (F5-SSLO Port-1.1 client-vlan), Dst: 52:54:00:a1:d6:6b (Client-MAC)
- IPv4, Src: 142.251.10.157 (adservice.google.com), Dst: 10.1.10.50 (Client-IP)
- TCP, Src Port: 443, Dst Port: 60838
- TLSv1.2, Handshake Type: Server Hello
- Random: c47f7..
- Session ID: a5c11..
- Cipher Suites: TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
- Extensions
- Elliptic curves point formats (ec_point_formats)
- Renegotiation info
- TLSv1.2, Handshake Type: Certificate
- Total Certificates Length: 4376 bytes
- Signed Certificate (3384 bytes)
- Serial Number: 0x6611ec89f1aa35db
- Signature Algorithm: sha256WithRSAEncryption
- Issuer
- commonName=subrsa.f5labs.com
- countryName=US | organizationName=f5labs.com
- Subject
- commonName=*.google.com
- Validity: notBefore 2024-03-04 06:35:50 (UTC) | notBefore 2024-05-07 00:44:57 (UTC)
- subjectPublicKeyInfo
- algorithm: rsaEncryption
- subjectPublicKey: modulus: 0x00994 | publicExponent: 65537
- Extensions
- extKeyUsage: KeyPurpose: id-kp-serverAuth
- basicConstraints: [Critical] BasicConstraintsSyntax [0 length]
- subjectAltName: *.google.com | *.appengine.google.com | …
- authorityKeyIdentifier: keyIdentifier: a23ea…
- Padding: 0
- Encrypted: 2a9a5…
- Signed Certificate (986 bytes)
- Serial Number: 0x02
- Signature Algorithm: sha256WithRSAEncryption
- Issuer
- commonName=f5labs.com
- countryName=US | organizationName=f5labs.com
- Subject
- commonName=subrsa.f5labs.com
- countryName=US | organizationName=f5labs.com
- Validity: notBefore 2019-02-27 10:51:48 (UTC) | notBefore 2030-05-16 10:51:48 (UTC)
- subjectPublicKeyInfo
- algorithm: rsaEncryption
- subjectPublicKey: modulus: 0x00b71 | publicExponent: 65537
- Extensions
- keyUsage:
- digitalSignature: True | keyCertSign: True | cRLSign: True
- dataEncipherment: False | keyAgreement: False | contentCommitment: False
- keyEncipherment: False | encipherOnly: False | decipherOnly: False
- basicConstraints: [Critical] cA: True
- subjectKeyIdentifier: a23ea…
- authorityKeyIdentifier: keyIdentifier: 4a101…
- keyUsage:
- Padding: 0
- Encrypted: 05655…
- TLSv1.2, Handshake Type: Server Key Exchange
- EC Diffie-Hellman Server Params
- Curve Type: named_curve | Named Curve: secp256r1 (0x0017)
- Pubkey (Length 65): 043ba…
- Signature Algorithm: rsa_pkcs1_sha256 (Hash: SHA256 | Signature: RSA)
- Signature (Length 256): 464ce…
- EC Diffie-Hellman Server Params
- TLSv1.2, Handshake Type: Server Hello Done
- F5 Ethernet Trailer Protocol
- Virtual Server: /Common/sslo_demoL3.app/sslo_demoL3-in-t-4
- Flow ID: 0x0000400001998e00 | Peer ID: 0x0000400001998700
- A. Client -> F5 SSLO VS (send “TLSv1.2 Client Hello” via client-vlan)
- ETH II, Src: 52:54:00:a1:d6:6b (Client-MAC), Dst: 52:54:00:8f:3c:03 (F5-SSLO Port-1.1 client-vlan)
- IPv4, Src: 10.1.10.50 (Client-IP), Dst: 142.251.175.104 (www.google.com)
- TCP, Src Port: 36530, Dst Port: 443
- TLSv1.2, Handshake Type: Client Hello
- Random: ef889..
- Session ID: 3e842..
- Cipher Suites (16 suites)
- …
- Cipher Suite: TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
- Cipher Suite: TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
- Cipher Suite: TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
- …
- Extensions
- server_name name=www.google.com
- supported_versions TLS 1.3, TLS 1.2, TLS 1.1, TLS 1.0
- Signature Hash Algorithms (8 algorithms)
- ecdsa_secp256r1_sha256 | rsa_pss_rsae_sha256 | rsa_pkcs1_sha256
- ecdsa_secp384r1_sha384 | rsa_pss_rsae_sha384 | rsa_pkcs1_sha384
- rsa_pss_rsae_sha512 | rsa_pkcs1_sha512
- Elliptic curves point formats (ec_point_formats)
- Renegotiation info
- PSK Key Exchange Mode: PSK with (EC)DHE key establishment (psk_dhe_ke)
- F5 Ethernet Trailer Protocol
- Flow ID: 0x00004001de570600 | Peer ID: 0x00004001de573200
2.3 HTTP Traffic Flow
Traffic Flow - HTTP Request- A. Client -> F5 SSLO VS (send HTTP_Request via client-vlan)
- ETH-II, Src: 52:54:00:a1:d6:6b (Client-MAC), Dst: 52:54:00:8f:3c:03 (F5-SSLO Port-1.1 client-vlan)
- IPv4, Src: 10.1.10.50 (Client-IP), Dst: 142.251.175.104 (www.google.com)
- TCP, Src Port: 36530, Dst Port: 443
- TLSv1.2 (payload is encrypted)
- HTTP: www.google.com | GET / HTTP/1.1 (decrypted via sessionsecret iRules)
- F5 Ethernet Trailer Protocol
- Flow ID: 0x00004001de570600 | Peer ID: 0x00004001de573200
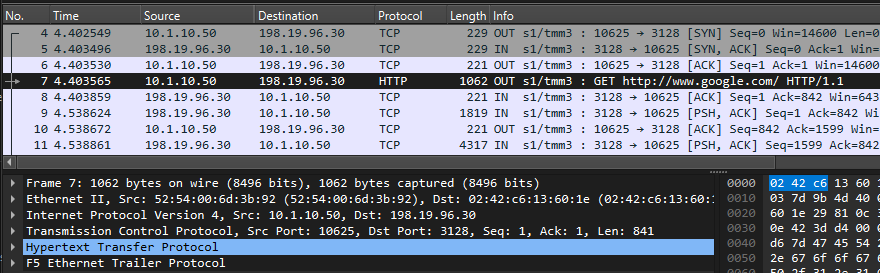
- B. F5 SSLO -> ssloS_Proxy (send HTTP_Request via Proxy_in)
- ETH-II, Src: 52:54:00:6d:3b:92 (F5-SSLO Port-1.3 ssloN_Proxy_in), Dst: 02:42:c6:13:60:1e (Proxy_HTTP_Device)
- IPv4, Src: 10.1.10.50 (Client-IP), Dst: 198.19.96.30 (Proxy_HTTP_Device)
- TCP, Src Port: 10625, Dst Port: 3128
- HTTP: www.google.com | GET http://www.google.com/ HTTP/1.1
- X-F5-SplitSession: AAMAAFQAAAAAAAAA
- F5 Ethernet Trailer Protocol
- Flow ID: 0x00004001de570400 | Peer ID: 0x00004001de571d00
- C. ssloS_Proxy -> F5 SSLO (send HTTP_Request via Proxy_out)
- ETH-II, Src: 02:42:c6:13:60:82 (Proxy_HTTP_Device_out), Dst: 52:54:00:6d:3b:92 (F5-SSLO Port-1.3 ssloN_Proxy_out)
- IPv4, Src: 198.19.96.130 (Proxy_HTTP_Device), Dst: 142.251.12.103 (www.google.com)
- TCP, Src Port: 39618, Dst Port: 80
- HTTP: www.google.com | GET / HTTP/1.1
- X-F5-SplitSession: AAMAAFQAAAAAAAAA
- Via: 1.1 XXX (squid/3.5.27) | X-Forwarded-For: 10.1.10.50
- F5 Ethernet Trailer Protocol
- Flow ID: 0x0000400140b71200 | Peer ID: 0x0000000000000000
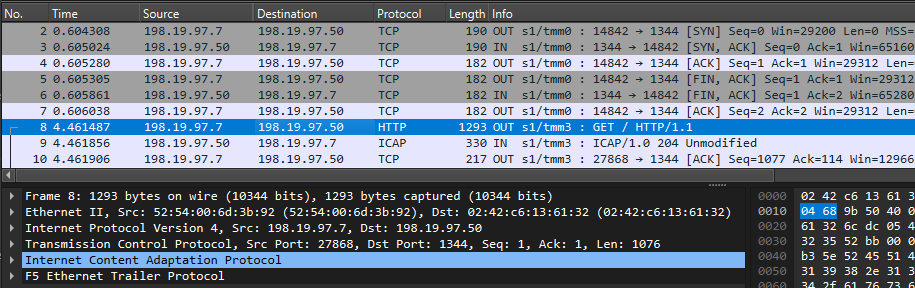
- D. (1) F5 SSLO -> ssloS_DLP (send [ICAP REQMOD] HTTP_Request via dlp-vlan)
- ETH-II, Src: 52:54:00:6d:3b:92 (F5-SSLO Port-1.3 dlp-vlan), Dst: 02:42:c6:13:61:32 (DLP_ICAP_Device)
- IPv4, Src: 198.19.97.7 (F5-SSLO dlp-self), Dst: 198.19.97.50 (DLP_ICAP_Device)
- TCP, Src Port: 27868, Dst Port: 1344
- ICAP
- REQMOD icap://198.19.97.50:1344/avscan ICAP/1.0
- Date: XX | Host: 198.19.97.50:1344 | Encapsulated: XXXX
- Preview: XX | X-Client-IP: 10.1.10.50
- HTTP: www.google.com | GET / HTTP/1.1
- Via: 1.1 XXX (squid/3.5.27) | X-Forwarded-For: 10.1.10.50
- F5 Ethernet Trailer Protocol
- Flow ID: 0x00004001de572c00 | Peer ID: 0x00004001de571300
- D. (2) ssloS_DLP -> F5 SSLO (reply with ICAP/1.0 204 Unmodified via dlp-vlan)
- ETH-II, Src: 02:42:c6:13:61:32 (DLP_ICAP_Device), Dst: 52:54:00:6d:3b:92 (F5-SSLO Port-1.3 dlp-vlan)
- IPv4, Src: 198.19.97.50 (DLP_ICAP_Device), Dst: 198.19.97.7 (F5-SSLO dlp-self)
- TCP, Src Port: 1344, Dst Port: 27868
- ICAP
- ICAP/1.0 204 Unmodified
- Server: C-ICAP/0.4.4 | Connection: keep-alive | ISTag: XXX
- F5 Ethernet Trailer Protocol
- Flow ID: 0x00004001de572c00 | Peer ID: 0x00004001de571300
- E. F5 SSLO -> ssloS_TAP (send HTTP_Request via TAP-in)
- ETH-II, Src: 52:54:00:df:67:7d (F5-SSLO Port-1.6 ssloN_TAP_in), Dst: 12:12:12:12:12:12 (TAP_Device_MAC)
- IPv4, Src: 10.1.10.50 (Client-IP), Dst: 142.251.175.104 (www.google.com)
- TCP, Src Port: 36530, Dst Port: 443
- HTTP: www.google.com | GET / HTTP/1.1
- Via: 1.1 XXX (squid/3.5.27) | X-Forwarded-For: 10.1.10.50
- F5 Ethernet Trailer Protocol
- Flow ID: 0x00004001de572b00 | Peer ID: 0x0000000000000000
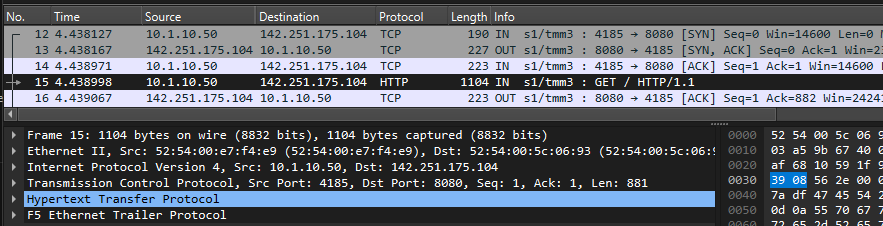
- F. F5 SSLO -> ssloS_FEYE (send HTTP_Request via FEYE_in)
- ETH-II, Src: 52:54:00:e7:f4:e9 (F5-SSLO Port-1.4 ssloN_FEYE_in), Dst: 52:54:00:5c:06:93 (F5-SSLO Port-1.5 ssloN_FEYE_out)
- IPv4, Src: 10.1.10.50 (Client-IP), Dst: 142.251.175.104 (www.google.com)
- TCP, Src Port: 4185, Dst Port: 8080
- HTTP: www.google.com | GET / HTTP/1.1
- Via: 1.1 XXX (squid/3.5.27) | X-Forwarded-For: 10.1.10.50
- F5 Ethernet Trailer Protocol
- Flow ID: 0x00004001de56fb00 | Peer ID: 0x00004001de570e00
- G. ssloS_FEYE -> F5 SSLO (send HTTP_Request via FEYE_out)
- ETH-II, Src: 52:54:00:e7:f4:e9 (F5-SSLO Port-1.4 ssloN_FEYE_in), Dst: 52:54:00:5c:06:93 (F5-SSLO Port-1.5 ssloN_FEYE_out)
- IPv4, Src: 10.1.10.50 (Client-IP), Dst: 142.251.175.104 (www.google.com)
- TCP, Src Port: 4185, Dst Port: 8080
- HTTP: www.google.com | GET / HTTP/1.1
- Via: 1.1 XXX (squid/3.5.27) | X-Forwarded-For: 10.1.10.50
- F5 Ethernet Trailer Protocol
- Flow ID: 0x00004001de56ff00 | Peer ID: 0x0000000000000000
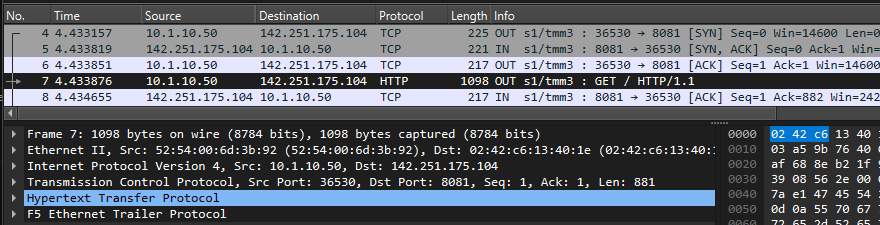
- H. F5 SSLO -> ssloS_IPS (send HTTP_Request via IPS_in)
- ETH-II, Src: 52:54:00:6d:3b:92 (F5-SSLO Port-1.3 ssloN_IPS_in), Dst: 02:42:c6:13:40:1e (IPS_L3_Device_MAC)
- IPv4, Src: 10.1.10.50 (Client-IP), Dst: 142.251.175.104 (www.google.com)
- TCP, Src Port: 36530, Dst Port: 8081
- HTTP: www.google.com | GET / HTTP/1.1
- Via: 1.1 XXX (squid/3.5.27) | X-Forwarded-For: 10.1.10.50
- F5 Ethernet Trailer Protocol
- Flow ID: 0x00004001de572200 | Peer ID: 0x00004001de56f400
- I. ssloS_IPS -> F5 SSLO (send HTTP_Request via IPS_out)
- ETH-II, Src: 02:42:c6:13:40:82 (IPS_L3_Device_MAC_out), Dst: 52:54:00:6d:3b:92 (F5-SSLO Port-1.3 ssloN_IPS_out)
- IPv4, Src: 10.1.10.50 (Client-IP), Dst: 142.251.175.104 (www.google.com)
- TCP, Src Port: 36530, Dst Port: 8081
- HTTP: www.google.com | GET / HTTP/1.1
- Via: 1.1 XXX (squid/3.5.27) | X-Forwarded-For: 10.1.10.50
- F5 Ethernet Trailer Protocol
- Flow ID: 0x00004001de56ff00 | Peer ID: 0x0000000000000000
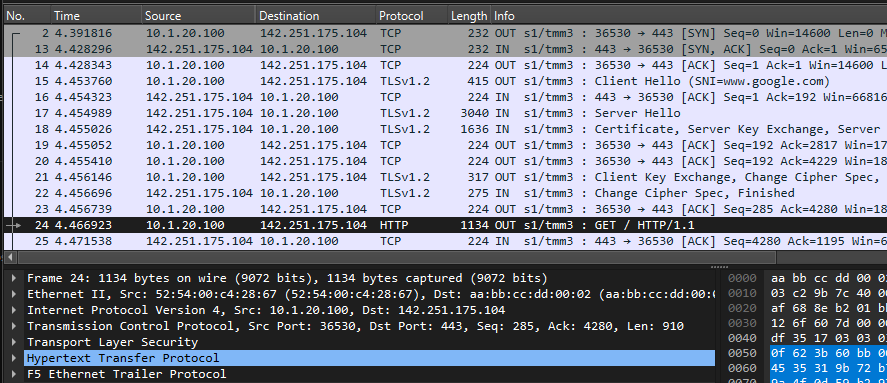
- J. F5 SSLO -> Internet (send HTTP_Request via outbound-vlan)
- ETH-II, Src: 52:54:00:c4:28:67 (F5-SSLO Port-1.2 outbound-vlan), Dst: aa:bb:cc:dd:00:02 (IPv4_Outbound_Gateways)
- IPv4, Src: 10.1.20.100 (SNAT_Auto_Map), Dst: 142.251.175.104 (www.google.com)
- TCP, Src Port: 36530, Dst Port: 443
- TLSv1.2 (payload is encrypted)
- HTTP: www.google.com | GET / HTTP/1.1 (decrypted via sessionsecret iRules)
- Via: 1.1 XXX (squid/3.5.27) | X-Forwarded-For: 10.1.10.50
- F5 Ethernet Trailer Protocol
- Flow ID: 0x00004001de573200 | Peer ID: 0x00004001de570600
- A. Client -> F5 SSLO VS (send HTTP_Request via client-vlan)
- B. F5 SSLO -> ssloS_Proxy (send HTTP_Request via Proxy_in)
- C. ssloS_Proxy -> F5 SSLO (send HTTP_Request via Proxy_out)
- D. F5 SSLO -> ssloS_DLP (send [ICAP REQMOD] HTTP_Request via dlp-vlan)
- ssloS_DLP -> F5 SSLO (reply with ICAP/1.0 204 Unmodified via dlp-vlan)
- E. F5 SSLO -> ssloS_TAP (send HTTP_Request via TAP-in)
- F. F5 SSLO -> ssloS_FEYE (send HTTP_Request via FEYE_in)
- G. ssloS_FEYE -> F5 SSLO (send HTTP_Request via FEYE_out)
- H. F5 SSLO -> ssloS_IPS (send HTTP_Request via IPS_in)
- I. ssloS_IPS -> F5 SSLO (send HTTP_Request via IPS_out)
- J. F5 SSLO -> Internet (send HTTP_Request via outbound-vlan)
Supplemental Links
- None